Identity Fraud Report: The Battle in the Dark
The Battle in the Dark Report 2025, created by Signicat and cybersecurity expert Lisa Forte, reveals a stark gap between business confidence and actual fraud readiness.
Drawing on insights from 900 fraud decision-makers across Europe, the report exposes overlooked threats, revenue loss, and outdated defences—making a clear case for urgent action to prevent identity fraud and strengthen identity fraud protection.

Most businesses think they’re ahead of identity fraud
In reality, they’re flying blind:
→ 59% report a rise in successful fraud
→ 1 in 5 transactions and onboardings are fraudulent
→ Just 45% measure its impact
→ 22% of revenue is affected by identity fraud and its prevention efforts
→ 80% say fraudsters adapt when blocked
→ 74% believe they’re winning—despite the numbers

Join the conversation
Explore the findings of the report in more depth. Watch Lisa Forte (Red Goat Cyber Security) and Pinar Alpay (Signicat) discuss the evolving tactics of identity fraud and what businesses can do to stay ahead.
What’s in the report
-
Insights from 900 fraud decision-makers
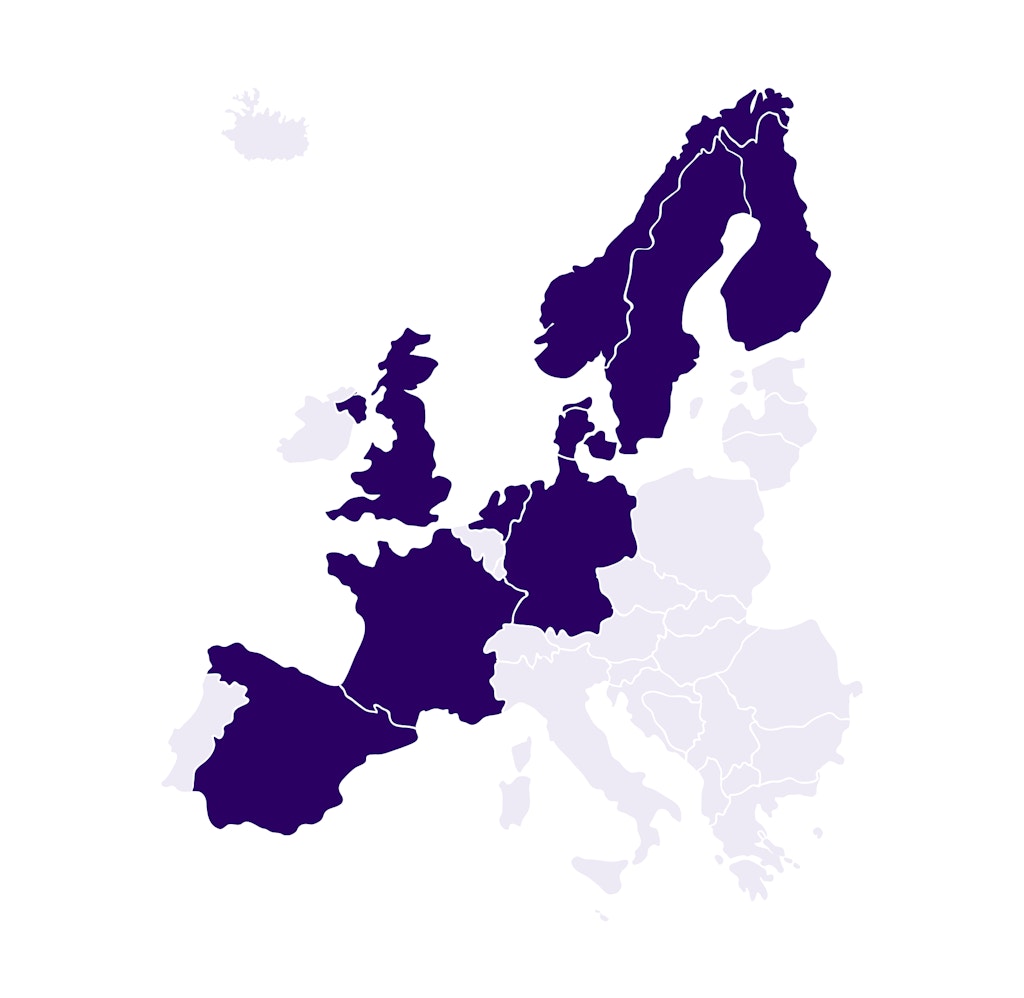
Covering Denmark, Finland, France, Germany, the Netherlands, Norway, Spain, Sweden, and the UK -
Fraud trends, risks, and vulnerabilities across banking, fintech, insurance, gaming, and automotive
-
How AI, deepfakes, synthetic IDs, and account takeovers are reshaping the threat landscape
-
The real cost of fraud: revenue loss, fraud exposure, and hidden weaknesses
-
Confidence is high, but many lack the tools and data to back it up
-
Practical steps to strengthen detection, visibility, and control—and to help prevent identity fraud more effectively

“Digital identity fraud, account takeover and synthetic ID fraud aren’t abstract threats. They’re happening now, and they’re targeting businesses that believed they had strong controls in place.”
— Lisa Forte, Partner @ Red Goat Cyber Security

Data Insights by Country
Select your key markets and get targeted data:
-
MitID offers solid protection, yet document forgery at onboarding remains a key gap. Confidence is high, but financial impact is higher.
-
Finland faces the steepest rise in both attempted and successful fraud. Account takeover and social engineering are on the rise during transactions.
-
France combines strong onboarding with rising identity fraud shifting to login and transactions, while reporting the lowest revenue impact at 14%.
-
Even with strict compliance, fraud grows as social engineering and account takeover exploit human and process gaps.
-
Fraud attempts are rising in line with Europe, but many organisations are flying blind. With only 35% measuring fraud impact, success rates are climbing under the radar.
-
Strong digital identity (BankID) keeps attempts low, but targeted attacks are increasingly successful, especially at the transaction stage.
-
Diverse identity systems create gaps. Social engineering and account takeover dominate, particularly at login and payment points.
-
BankID secures onboarding, but fraud is shifting to document forgery, login and transaction stages, where overconfidence may hide new risks.
-
Technology is the UK’s main fraud target, with identity attacks hitting around 22% of revenue as fraudsters exploit onboarding and tech gaps.
Data Insights by Industry
Select your key industries and get targeted data:
-
Banks see 70% more attempts and 64% more successful attacks, with identity fraud hitting 21%+ of revenue as risk shifts from KYC to logins and payments.
-
Gaming reports 59% more attempts and 60% more successful attacks, with identity fraud impacting 28.6% of revenue and 48% of cases targeting eID technologies.
-
Insurers face rising attempts (52%) and successes (59%), and identity fraud now affects 28% of revenue across applications, logins and claims.
-
Attempts are up 54% and successes 59%, with identity fraud affecting 17% of revenue and peaking at the transaction stage across rentals, leases and delivery.
-
67% of firms report more attempts and 54% more successes, with identity fraud impacting 16% of revenue and half of attacks clustering at the transaction stage.
